Ken Grady explains why many commonly used password policies provide very little protection, and he shares the new approach he has implemented as CIO at New England BioLabs.
I had been in my job here exactly 6 months. How did I know? Because my password had just expired according to the company’s password policy. So, I had to reset it, and reteach my muscle memory the chosen new password for the next two weeks, swearing softly (or not so softly) under my breath every time I logged in.
I recently oversaw a change in password policy at my company. To be fair though, the old policy was not that far off the “norm”:
- Required changing twice a year
- Minimum of 7 characters
- It couldn't contain your first name or last name.
- When changing it, you couldn't repeat any of your last 3 passwords.
- It had to contain at least 3 of the following 4:
- An upper case letter
- A lower case letter
- A number
- A special character ($, !, *, etc)
This is fairly typical of the password policies you find at most corporations. And I've definitely seen worse. But with these policies, all most IT departments succeed at is making users write their passwords down on a sticky note, or place calls to the Help Desk unnecessarily.
"And by the way, changing the password every so often does absolutely nothing to make you more secure. " |
This isn't to say that requiring passwords is a bad idea: identity theft and theft of intellectual property are increasingly common. You hear about it all the time on the news these days (which is another indication that most password policies are ineffective).
You just need a good password policy. And by the way, changing the password every so often does absolutely nothing to make you more secure. Changing the password only helps if it was already hacked. It doesn’t change the math required to hack it in the first place, and offers little to a company like ours besides increasing the number of help desk calls we receive. That’s why, to me, that requirement in a password policy seems useless and unnecessary.
READ THIS PART IF YOU LIKE MATH
The overall complexity of a password can be calculated and expressed in mathematical terms. To understand what makes a good password (at work or at home), mathematicians and security people talk about the concept of "entropy." In essence, it's the algorithm that combines the total number of possibilities for each character, and the total number of characters, and figures out how long it would take to go through them to get the right one.
With our old password policy, the complexity, or "entropy", as expressed in mathematical terms of my password hovered around 7.56 * 10^12. Which sounds like a fairly big number, right?
Not so much. Such passwords take about 2 days to break through using run-of-the-mill hacking programs downloaded off the internet (I wish I was making that up). It would take less than 2 minutes for a reasonably modern hacking algorithm to break.
READ THIS PART IF YOU ONLY LIKE MATH WHEN IT COMES WITH PICTURES
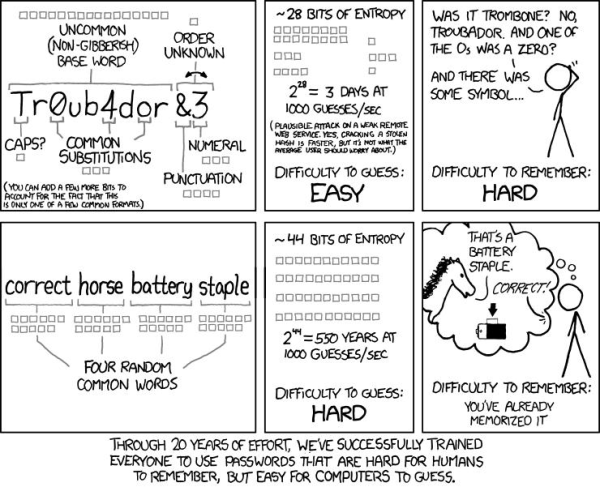
(Image Credit: xkcd.com)
Here is the new password policy I have since implemented here.
Computer passwords are required to be at least 20 characters long.
That's right. 20. Spaces count. Trust me, it’s not as crazy as you think. And once we explained it, everyone was fine with it. Our users can make nifty little sentences they’ll never forget, and special characters or numbers aren’t required. They are exponentially harder to break than their old passwords. Here are some good acceptable examples:
• I have really bright children (30 Characters. Complexity: 9.08 x 10^55)
• Tom Brady is super dreamy (25 Characters. Complexity: 1.74 x 10^48)
• Watch out for terrapins (23 Characters. Complexity: 2.41 x 10^44)
• I am methylation sensitive (26 Characters. Complexity: 1.48 x 10^50)
Don’t worry about calculating the exact password complexity. I just did that above for illustrative purposes. The important thing is that the number is crazy-high compared to what's possible with typical password policies. (For comparison, the complexity of our old passwords was 7.56 * 10^12).
This policy is exponentially more secure, and every example shown above is far easier to remember than a typical password.
And perhaps the best part is that passwords need never expire! As mentioned above, that policy adds nothing to the overall security.
Along with ensuring every authorized device has a digital certificate, this has created a much more secure and stable policy, backed up by reasons that our users understand and can get behind. They no longer experience the frustration of changing and forgetting their passwords, and we have reduced calls to the Help Desk.
It's not exactly peace in the Middle East but it certainly will make life a little easier, and more secure, for our users.


Add a Comment